Online Security Checklist
How to protect your privacy online
- Don't include sensitive information in email
- Never click on unknown links within an email
- Don't open SPAM or attachments from strangers
- Be suspicious of emails asking for personal information
- Be selective when providing your email address
- Only open email and attachments from known senders
Offline Security Checklist
How to protect your privacy at home
- Monitor your postal mail
- Don't give out your personal information freely
- Check your credit report annually
- Shred documents containing personal information before discarding them
Protect Your Account
Scammers are constantly coming up with new ways to trick people into giving out sensitive information. Learn more about how to spot financial scams.
Email Scams
-
Delete all spam without opening it. Responding to spam only confirms your email address to the spammer, which can intensify the problem. Additionally, fraudulent emails send out urgent messages that claim your account will be closed if sensitive information isn't immediately provided, or that important security information needs to be updated online. Your financial institution will never use this method.
-
If you do not know the sender, or are not expecting the attachment, delete it. For attachments most computer files use filename extensions such as “.doc” for documents or “.jpg” for images. If a file has a double extension, like “heythere.doc.pif,” it is highly likely that this is a dangerous file. For links it’s safer to retype the web address than to click on it.
-
Forged emails falsely claiming to be from your financial institution or favorite online store is a popular trick used by criminals to extract personal information for fraud. It is also a good idea to not send security passwords or one-time pass codes over email.
-
Typos and grammatical errors are tell-tale signs of a fraudulent email or website, as are unprofessional design layout and quality. Delete these emails immediately.
Mobile Security
-
Your phone should have a password protection option available that requires a password to access any information on the phone. This can be in the form of a true pattern unlock or an alphanumeric PIN to unlock the device. This makes it much more difficult for unauthorized access to your information if lost or stolen.
Some providers or manufacturers offer tracking services in the event your device is stolen or lost, which could include the ability to remotely delete stored information on the device. -
Similar to your computer, your mobile device needs to be up to date. Regularly check and update the operating system and apps to ensure security. Check your device manual or provider for more information.
-
Misconfigured wi-fi can be risky when accessing sensitive information or conducting business transactions. Be cautious when using public wi-fi and/or Hotspots, especially when connecting to banking, or other official business.
Only access apps and sites that are reputable and well-known. This is especially important for financial apps and sites. Always check to make sure you are using your known financial institution's official app or website. If you need clarification, call or email to confirm. -
Never send personal information over text messages or email. This includes, but is not limited to, usernames, passwords, dates of birth, Social Security numbers, account numbers or membership numbers.
Phone Scams
-
Phone scams are no joke, and scammers target millions every year. Watch out for scam attempts involving free vacations or prizes, technical issues with your device, missed payments or government/phony debt collectors, fake charities, warrant threats on you or a loved one, and medical alerts.
-
We will never send unsolicited messages or calls asking for your username, password, Social Security Number (SSN), or PIN. Banks may need to verify information if you call them, but never the other way around.
-
These are scams used by criminals to exploit a person's trust to obtain money directly or obtain confidential information. You may be tempted by false sense of urgency or distracted by background noise. There are many tactics scammers use within social engineering to pressure information out of you.
-
Whether a scammer has contacted you and is impersonating someone or it is a real call, stay on the safe side and end the call. Find the number that you have associated with the entity that is attempting the call and contact them yourself instead.
Fraud and Phishing
-
Fraud and phishing scams are common across all industries and can be used to target you. Be on the lookout for spoof calls, account takeover messages, online shopping, fake check requests, romance scams or economic impact payments. These all often involve requesting money to be sent, a change in your personal information or threats made to your accounts. Additionally, be wary of notifications or phone calls informing you a virus or issue has been detected on your device.
-
Worried that a link you clicked on may be a scam? If you’re worried you may have fallen victim to a scam, follow these steps to prevent additional fraud. Use Landmark’s phishing reporting tool.
-
Refrain from any continued interaction with the scammer.
-
Do not give out any additional personal information or money.
-
Gather all the information you know about the scam so you can report it clearly.
-
Run a security scan on your devices and delete anything identified as a problem or contact your service provider for assistance.
-
Change the username and password of the affected account.
-
Report the scam to your financial institution.
-
-
Always stay vigilant and take proper steps to prevent potential fraud or phishing. Tactics like updating your security software, locking, signing out, or shutting down your computer or device, using secure browsers, creating strong passwords, and utilizing multi-factor authentication can add roadblocks in a scammer’s path.
-
Scammers may try to impersonate a government agency or even a loved one to gain access to your account. Use Landmark resources and be aware of the most common types of scams so you can recognize them right away.
Examples of Phishing Scam Texts
Below are some samples of recent phishing scams. Report suspected phishing messages like the samples below, to Landmark's Security Team.
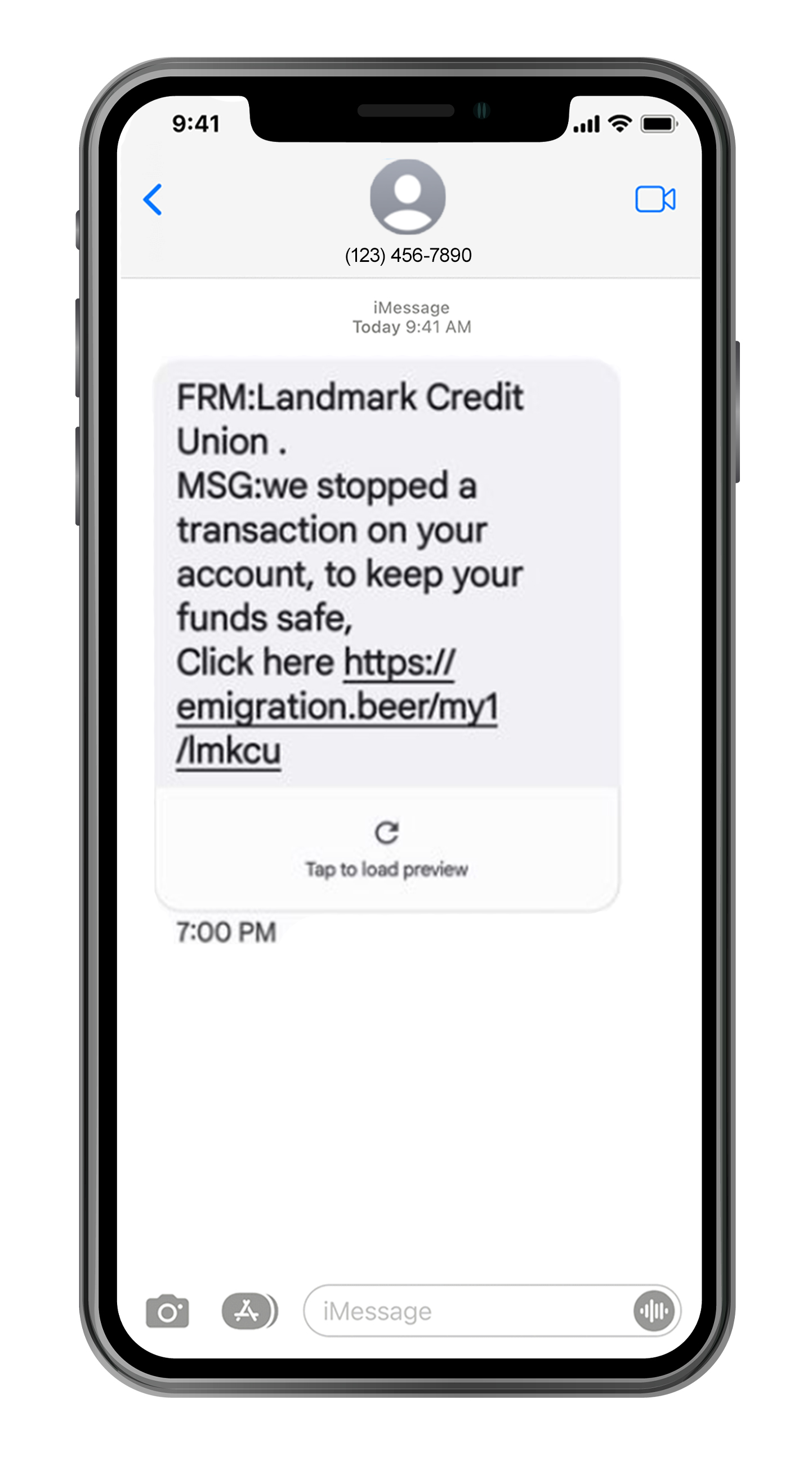
Debit Collection
A text or email phishing attempt to state a debit posted to your account. Do not click the link!
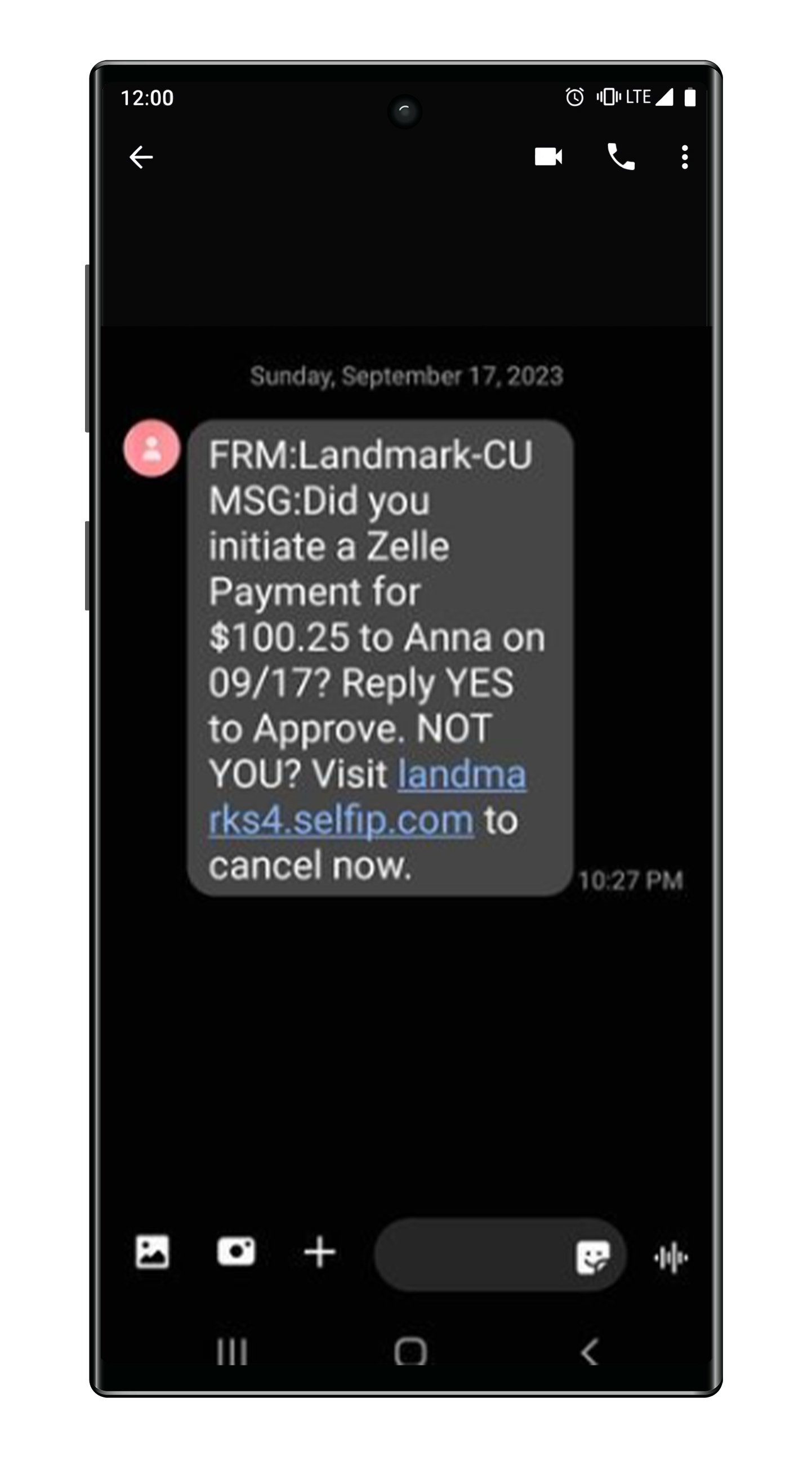
Suspended Account
A text or email phishing attempt that notifies you of suspended activity or unusual behavior on your account. Do not click the link!
Debit Pin Number Change
A text or email phishing attempt that asks you to change your debit card pin number on your account. Do not click the link!

How Landmark Protects You
Your online security is always our top priority. We have taken several steps to keep your information safe while accessing your account, but there are things you can do to protect your information as well. Learn about the steps we’ve taken online and additional ways you can continue preventing identify theft or fraud.
-
Antivirus solutions are designed to prevent, detect, and remove malware such as viruses, spyware, adware, and other forms of threats. Our solution is updated regularly and ensures fraud prevention and early detection of potential threats to keep your information secure.
-
Our intrusion detection system monitors our system and network to detect malicious activities or privacy violations to stop an intrusion. This allows us to log and report the incidents for continued security and watch for future threats.
-
SSL: or secure socket layer, is technology that protects our website and allows you to enter personal information through a private communication channel that is encrypted. This allows the data to remain secure during transmission. We use the most trusted SSL certificate available, an Extended Validation SSL certificate, which provides an extra layer of protection to you by requiring third-party Certificate Authorities (CA) to follow a strict issuance and management process for certificate approval and delivery.
Firewalls: The Internet requires computers to communicate and pass data or "packets" back and forth. Firewalls analyze these data packets and determine whether they should be allowed through. It essentially creates a "wall" between computers to block unwanted or malicious data. Our firewall creates a secure network to ensure a safe and trusted experience on our website.
-
We require strong login credentials to enhance your security. This includes using alphabetical (case sensitive), numeric and special characters and setting username and password length requirements.
We require identity verification in the form of a one-time passcode to login from a new computer or device. The one-time passcode is sent via text or phone call to confirm your identity and protect you from unauthorized login attempts.
Secure Your Finances
Risk Mitigation
Additional Cyber Security Videos & Resources
Enhance your detection & fraud prevention knowledge
View the following videos to gain more insight
Phishing
Phishing is a scam that involves the use of replicas of existing web pages that try to deceive you into entering personal, financial or password data. Often suspects use urgency or scare tactics, such as threats to close accounts.
Identity Theft
The impact of identity theft and online crimes can be greatly reduced if you can catch it shortly after your data is stolen or when the first use of your information is attempted.
Internet Fraud
It’s not always easy to identify online fraud, but cybercrime prevention can be straightforward. When you're armed with some technical advice and basic security awareness, you can avoid many attacks.
Social Media
Social media sites such as Facebook, Twitter, LinkedIn, Instagram and more are used by an extremely large volume of people, including cyber criminals, every day. Keep your information secure by limiting the amount of personal information you share.
Portable Devices
Portable devices include laptops, phones, tablets and more. These devices are very helpful, but they also contain personal information and could easily be lost or stolen. Know which steps you can take to protect yourself from the security risks that come along with portable devices.

Other Fraud and Security Resources
With all the resources available on the Internet, it can be difficult to determine which are the best. To make it as easy as possible for you, we've put together a short list of websites we've found to be the most helpful.
Check the resources below for more information about fraud and identity theft:
